Lesson 4: Overseeing Security Posture #
This lesson goes over the following:
- Viewing vulnerability reports and pages
- Viewing audit events
- Viewing the Software Bill of Materials (SBOM)
Viewing vulnerability reports and pages #
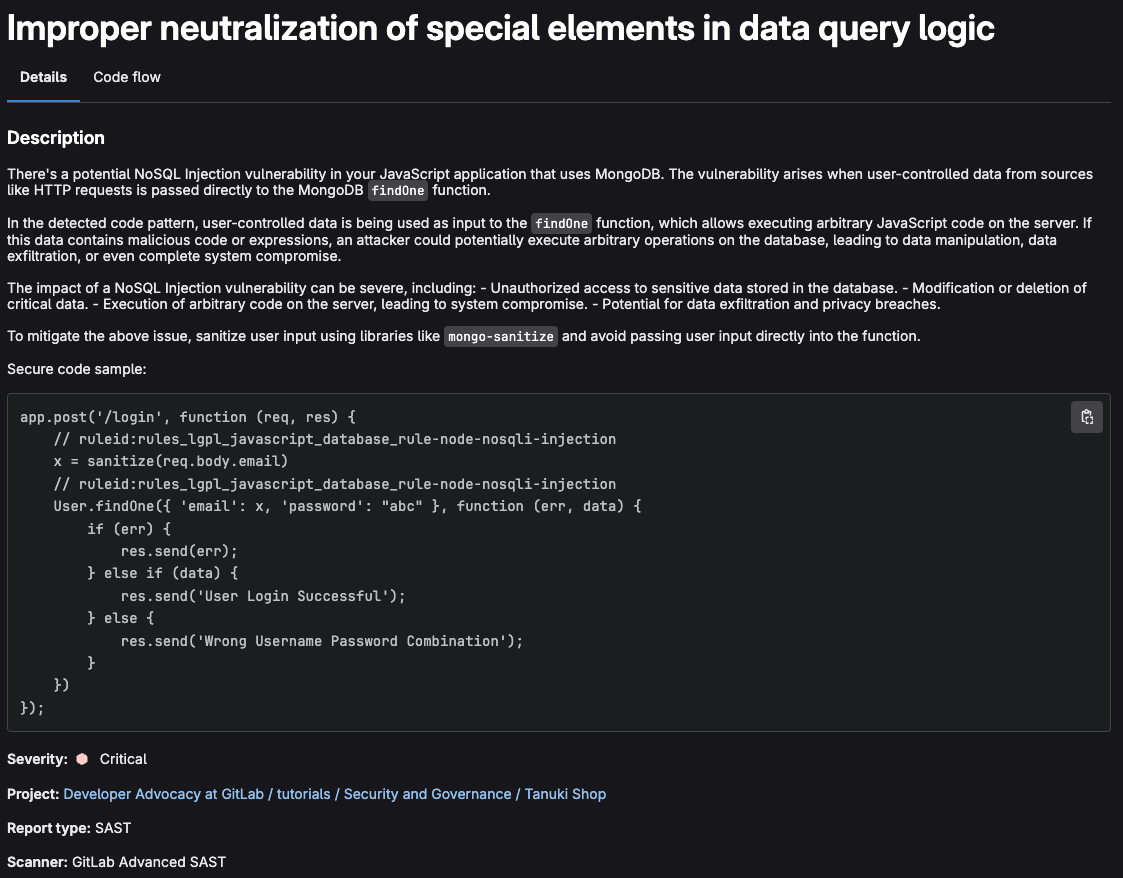
Each vulnerability report contains vulnerabilities from the scans of the most recent branch merged into the default branch. The vulnerability report displays the total number of vulnerabilities by severity, and when clicking on a vulnerability you are take to it’s vulnerability page providing with the following data:
- date
- status
- risk assessment data (severity, CVE, EPSS, KEV)
- description
- identifier
- the scanner where it was detected
- location
- activity (including related issues or available solutions)
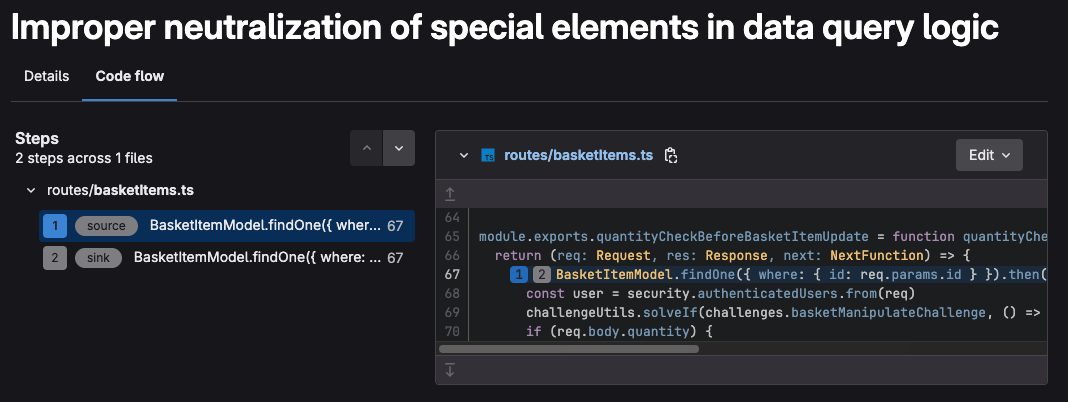
- codeflow (with advanced sast)
- comments
Navigate to Secure left navigation menu and select Vulnerability report
Set the filter to Group by: Tool
Expand SAST List
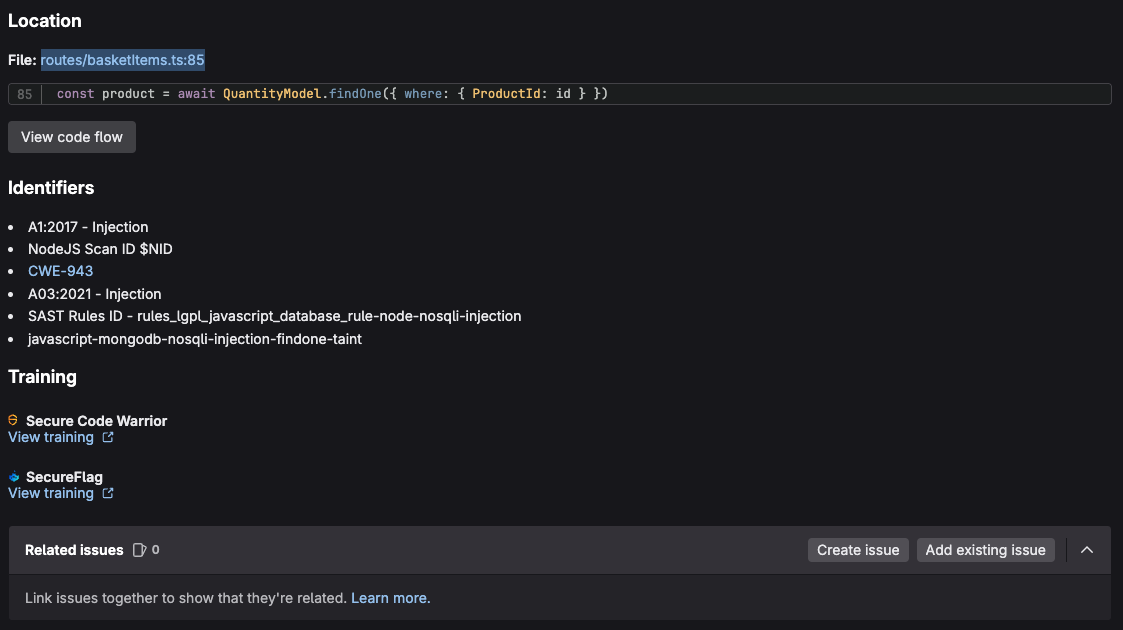
Click the description for Improper neutralization of special elements in data query logic with path routes/basketItems.ts:85, You should see detailed data on the vulnerability
- Select Code flow tab to see the detailed flow of the vulnerability
Select the Edit vulnerability box
Select Change Status
Select a status and add a comment, the press the Change Status button
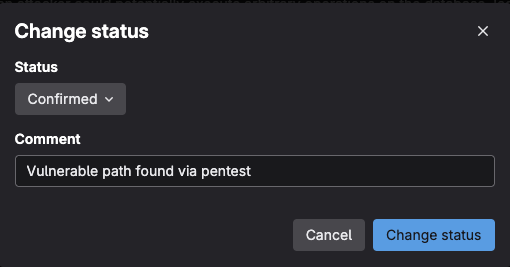
The status has now been changed allowing security teams to better sort through and manage vulnerabilities currently in the default branch
Scroll to the bottom ad press the Create Issue button, this will take you to an issue creation prompt which allows you to create an issue (confidential or not) in order to collaborate with developers on a resolution
Fill anything you want, scroll down, and click on the Create Issue button, you’ll then have an issue which can be used for AppSec and Development teams to collaborate on resolving the vulnerability
Viewing audit events #
Audit Events track important events, including who performed the related action and when. You can use audit events to track, for example:
- Who changed the permission level of a particular user for a GitLab project, and when.
- Who added a new user or removed a user, and when.
You can see a list of available Audit Events in the documentation.
Navigate to Secure left navigation menu and select Audit events
Look over the logged events
You can also stream these Audit Events to another tool or endpoint to process them. You can write functions to raise alerts on certain events and much more. See the [Audit Event Streaming documentation](https://docs.gitlab.com/ee/administration/audit_event_streaming.html) for more info.
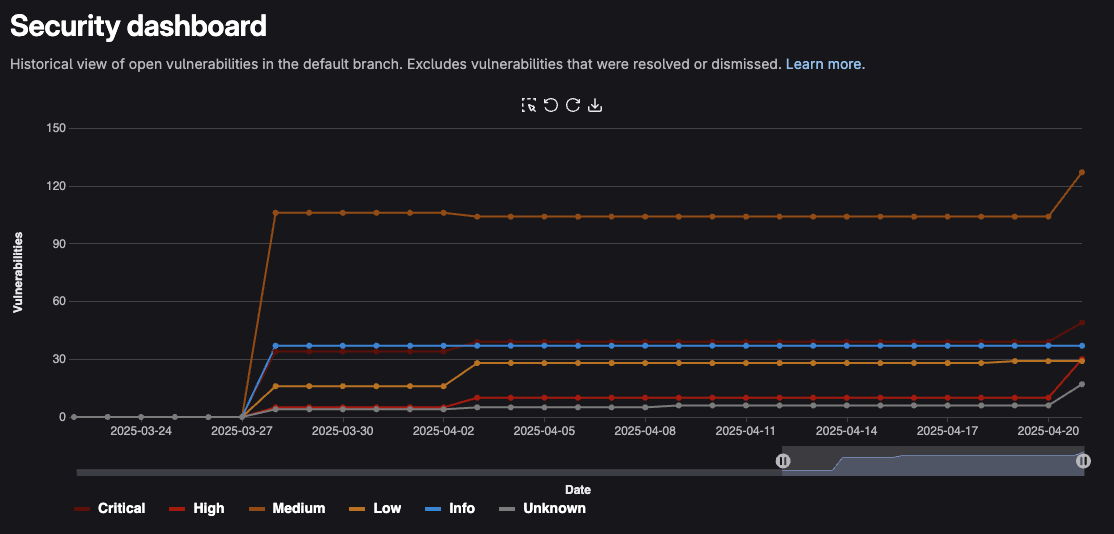
Accessing the security dashboard #
At the project level, the Security Dashboard displays a chart with the number of vulnerabilities introduced to the default branch over time.
- Access the Security Dashboard by going to Secure left navigation menu and selecting Security Dashboard
Nothing will be present, wait a day for it to be populated. Eventually over time with new commits introducing and resolving vulnerabilities
Viewing the Software Bill of Materials (SBOM) #
GitLab generates a Software Bill of Materials (SBOM) based on the latest successful scan on the default branch. An SBOM is a nested inventory, a list of ingredients that make up software components.
In GitLab we refer to an SBOM as a Dependency List. The dependency list shows the path between a dependency and a top-level dependency it’s connected to, if any. There are many possible paths connecting a transient dependency to top-level dependencies, but the user interface shows only one of the shortest paths. It requires:
- The Dependency Scanning or Container Scanning CI job must be configured for your project.
- Your project uses at least one of the languages and package managers supported by Gemnasium.
- A successful pipeline was run on the default branch
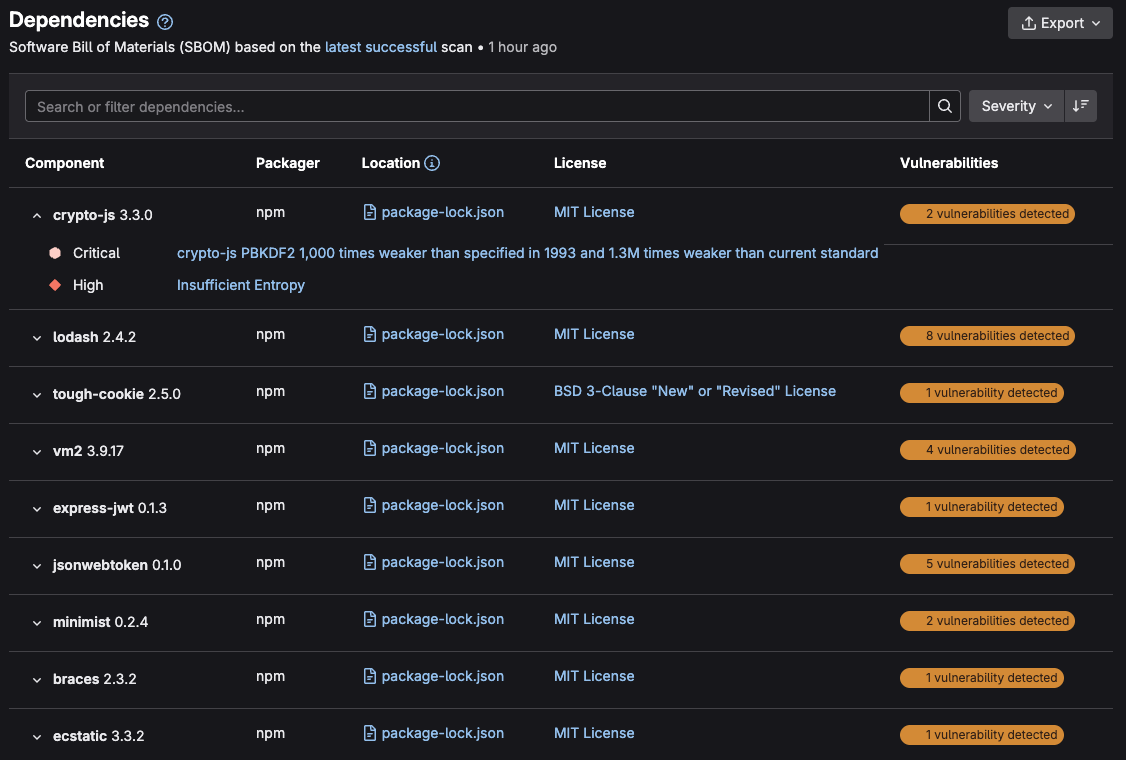
Navigate to Secure left navigation menu and select Dependency list
Examine the dependencies present, and look over the provided information:
- Component: The dependency’s name and version.
- Packager: The packager used to install the dependency.
- Location: For system dependencies, this lists the image that was scanned. For application dependencies, this shows a link to the packager-specific lock file in your project that declared the dependency.
- License: Links to dependency’s software licenses.
You can also download the SBOM in CycloneDX[1] format by looking at the artifacts generated within the Dependency Scanning Job. For more information on this, see the Dependency Scanning CycloneDX documentation[2] [1] https://cyclonedx.org/ [2] https://docs.gitlab.com/ee/user/application_security/dependency_scanning/#cyclonedx-software-bill-of-materials
Now that we have successfully gone over how AppSec teams can manage their security posture, we will cover GitLab Duo (AI) security features.