Developer Security Workflows #
This lesson goes over the following:
- Creating a merge request (MR) with vulnerable code
- Viewing the security policies
- Viewing and taking action on vulnerable code
- Viewing denied licenses
- Viewing injected compliance jobs
Creating a merge request (MR) with vulnerable code #
Now let’s go ahead and create an MR with vulnerabilities, by using the add-vulnerabilities branch. This branch contains several different types of vulnerabilities, the changes can be seen in this MR.
In the side tab, select Code > Merge requests
Press the New merge request button
Select add-vulnerabilities as the source branch
Select main as the target branch
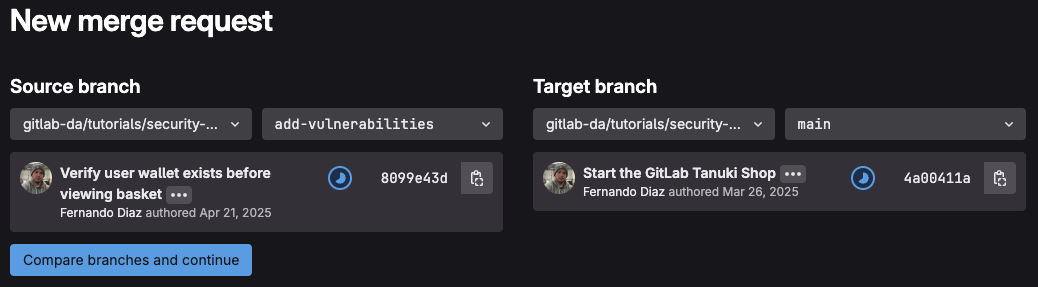
Press the Compare branches and continue button, you’ll be redirected to the New merge request page
Scroll down and press the Create merge request button, this will create a new merge request and the pipeline will run
Viewing the security policies #
Go to the merge request you created in step one
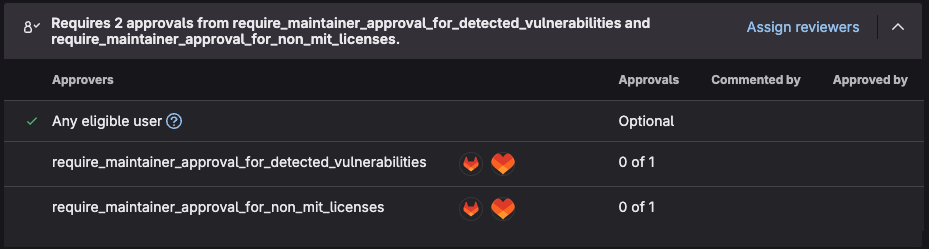
Expand the Requires 2 approvals tab
You should see that the policies we created are active and that approval is required since vulnerabilities and incompatible licenses were detected
Viewing and taking action on vulnerable code #
Now we can view the vulnerabilities after the pipeline started above has completely run. Let’s dig into the vulnerabilities and perform some actions on them.
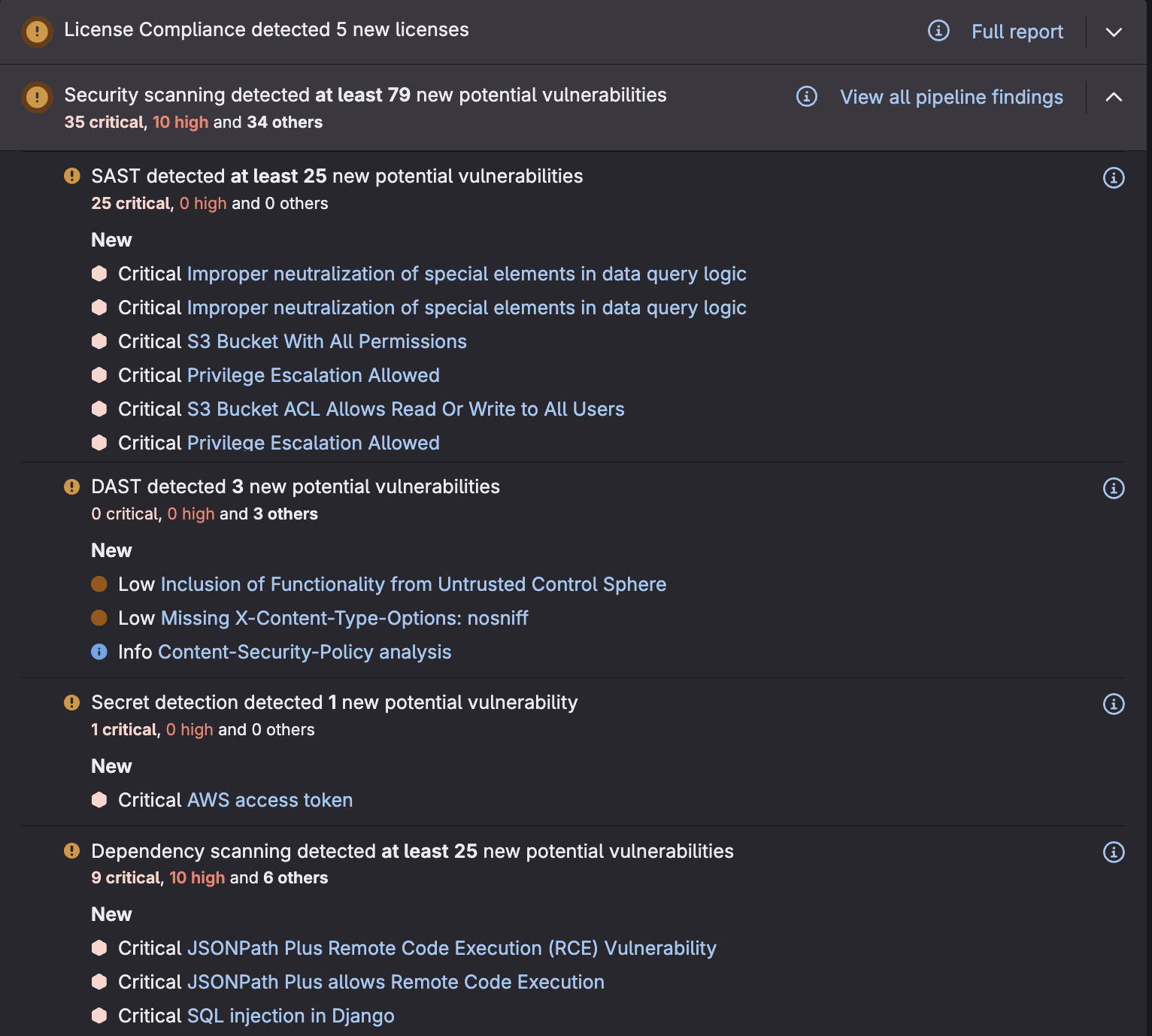
Within the merge request, press Expand in the Security scanning section
Scroll through the vulnerabilities and notice how each vulnerability is sorted by its scanner
- Click on any of the detected vulnerabilities and a popup will open with additional info
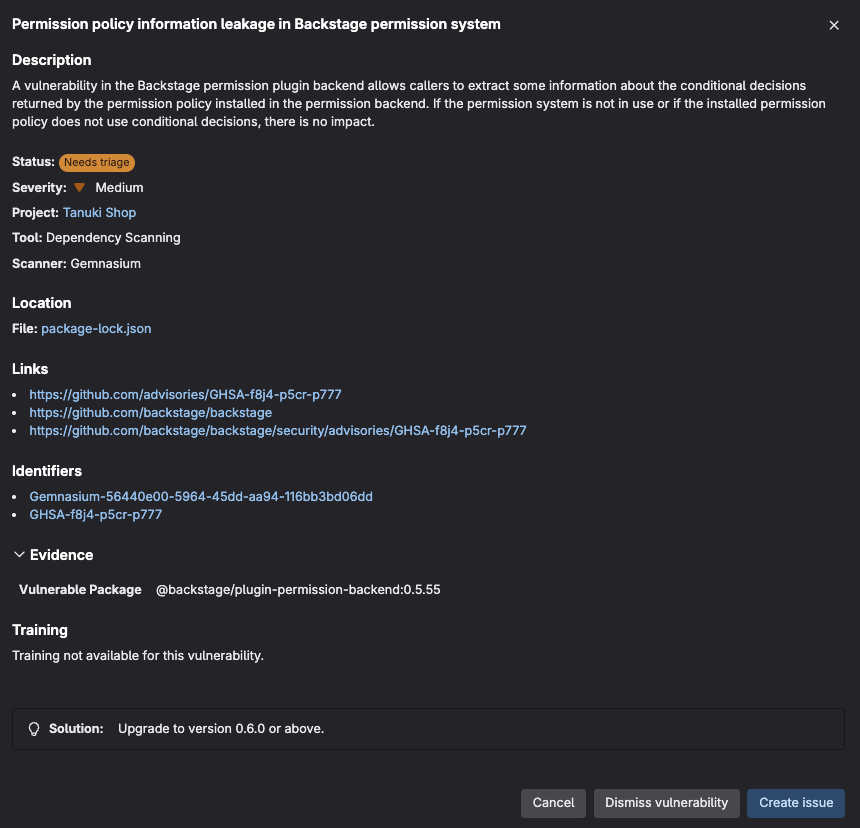
- Within the popup, dismiss the Vulnerability by clicking the Dismiss vulnerability button
This allows AppSec teams to see what developers are dismissing as well as why. If this MR were to be merged, then the vulnerability will automatically be tagged as dismissed in the vulnerability report
Click on the same vulnerability to see the popup again
Click on Create issue
This creates a confidential issue to allow developers and the security team to work together to resolve a vulnerability without displaying it to others (possibly malicious actors)
- Now go back to the Merge Request by pressing the back button on your browser
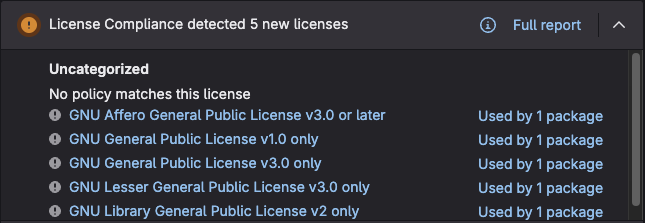
Viewing denied licenses #
Within the same MR view, we can see the licenses that were detected. You’ll be able to see which licenses are approved and denied according to the policy we set in an earlier lab.
Within the merge request, press Expand button in the License Compliance section.
Look over all the detected licenses which are shown as Denied since they are not MIT licenses
Viewing injected compliance jobs #
Now lets take a look at the custom compliance job we injected.
Click on the pipeline icon
Select the
soc2_compliance_checkjob in theteststageSee the echo output “SOC2 Compliance Check” which is injected from a separate yaml file containing separate permissions
Now that we have successfully gone over the DevSecOps workflows a developer takes part in, we can move on to how AppSec teams can monitor and act to enhance their organizations security posture.